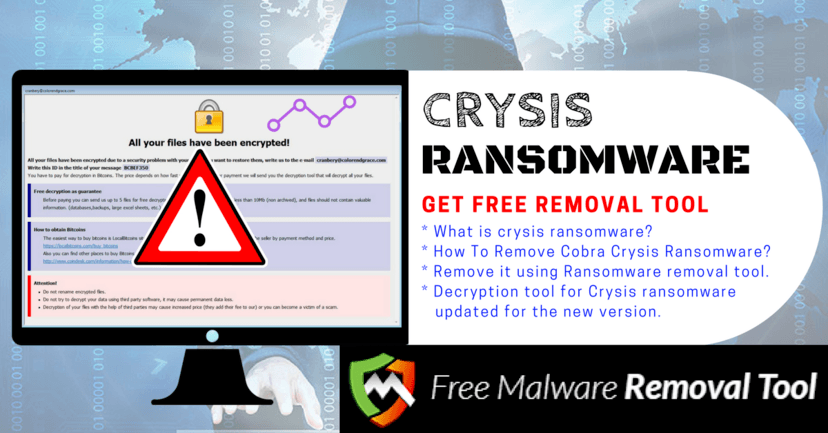
Vurten ransomware is a sort of infection found by malware security scientist, S!Ri. How might you come to know whether your PC is tainted – it is very basic as Vurten ransomware scrambles the greater part of your put away records and annexes filenames with the “.enhanced” augmentation (e.g., “sample.jpg” is renamed to “sample.jpg.improved”).
Also See: Adware Removal Tool Guide (Develop by Experts)
Scrambled records end up unusable. Instantly after encryption, Vurten creates a content document (“UNCRYPT.README.txt”) and spots it on the work area with a payoff note.

Basic Technique for This Ransomware to Influence Your PC.
The most widely recognized ransomware dissemination technique is spam email messages.
The principle point of these spam email battles conveys a great deal of messages with the ransomware installers covered up inside, and a portion of those aimlessly sent message achieve their objectives.
Other than spam email connections, Vurten Ransomware is additionally circulated straightforwardly through debased Remote Desktop Protocol.
At the point when malware makers utilization of this technique, the disease rate is normally little and nearby target.
Be that as it may, despite everything it needs clients to dispatch the disease record themselves, so please make a special effort to be caution at whatever point you get any new archive document.
Also See: Mini Militia Hacks
New establishment can be a strategy that this ransomware got inside your framework, which the client passed up a great opportunity without totally experiencing the permit assentions, terms, and condition.
The vast majority of them happen when you share documents like music, photographs and numerous more in the systems administration condition, going to different grown-up sites are additionally at risk for the inclusion of this danger inside your framework.
- Packaging: Most of the disease comes through outsider installers by concealing itself in freeware application. It comes covered up with a free application facilitated from a problematic site. At whatever point the casualty is uninformed of this terrible ransomware are, is covered up and introduced with any of these free application, at that point most likely this disease gets installed consequently.
- Downpours and P2P File Sharing: Online Ads are another normal offender. Deluge destinations particularly are outstanding for their traps including different phony download catches. On the off chance that you tap on the wrong catch, you’ll get a document to download that is named precisely like the record you need. Lamentably what’s inside is the infection.
Usual Way of Doing Things of Vurten Ransomware
When this pernicious payload of this record scrambling infection gets embedded on your gadget, it immediately starts PC checking for looking through the particular document composes put away on casualty’s framework keeping in mind the end goal to encode them as right on time as could be allowed and afterward requests a heavy total of payoff expense.
Commanded: Packers and Movers in Salt Lake
Besides, Vurten Ransomware runs unsafe contents through Command Prompt so as to root itself profound into the introduced working framework by utilizing the regulatory benefits and afterward empower AES-256 cryptography calculation.
Meanwhile, the decryptor offered by this malware costs is a precarious $10,000 which is one of the most noteworthy payoff expense requested by any ransomware infection in year 2018.
To debilitate the exploited PC clients, administrators of Vurten Ransomware gives seven days to make the payment installment.
Must Read: Rashtriya Swayamsevak Sangh (RSS)
Most imperative, security investigator’s recommendation not to pay the asked deliver expense, not on the grounds that the sum is high, but rather additionally there is a hazard that convicts may not give you to right decoding key regardless of whether you make the fruitful payment installment.
In this manner, expelling Vurten Ransomware ought to be your initial step and after that utilizing elective strategy for document recuperation will be your second steps keeping in mind the end goal to recoup yourself from the assault of such horrible digital dangers.